News Blast
Your daily source for breaking news and insightful articles.
Cybersecurity: Your Digital Bodyguard in a World Full of Intruders
Protect your digital life! Discover essential cybersecurity tips to guard against today's intruders and keep your online presence safe.
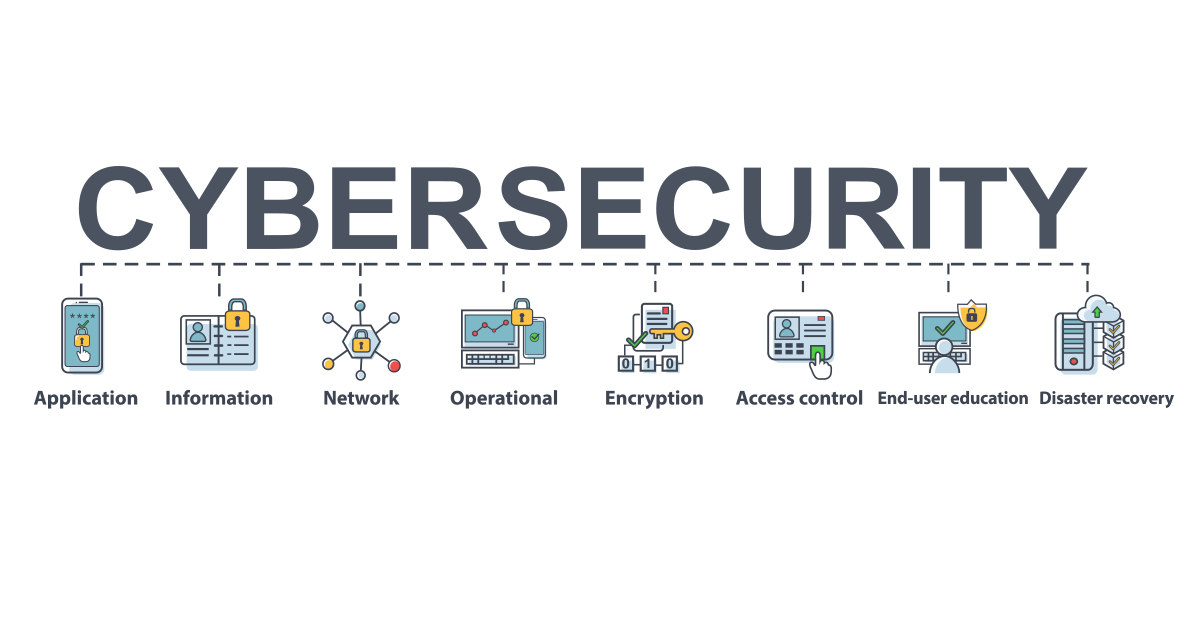
Top 5 Cybersecurity Threats and How to Protect Yourself
In today's digital age, understanding the top 5 cybersecurity threats is crucial for anyone looking to protect their personal and financial information. These threats include phishing attacks, where cybercriminals impersonate legitimate organizations to capture sensitive data; ransomware, which encrypts your files until a ransom is paid; malware, harmful software designed to disrupt, damage, or gain unauthorized access to systems; social engineering, where attackers manipulate individuals into breaking security protocols; and data breaches, which occur when unauthorized parties gain access to sensitive data. Recognizing these threats is the first step in defending against them.
To effectively protect yourself from these cybersecurity threats, consider implementing the following strategies:
- Enable two-factor authentication on all your accounts to add an extra layer of security.
- Regularly update your software and devices to ensure you have the latest security patches.
- Be cautious with emails and messages from unknown sources; always verify the sender before clicking on links or downloading attachments.
- Back up your data frequently to minimize losses in case of a ransomware attack.
- Educate yourself and your team about the latest cybersecurity threats and best practices to stay informed and vigilant.
Understanding the Importance of Firewalls: Your First Line of Defense
Firewalls are essential components of modern cybersecurity, serving as your first line of defense against unauthorized access and cyber threats. By monitoring and controlling incoming and outgoing network traffic based on predetermined security rules, firewalls act as a barrier between a trusted internal network and untrusted external networks. Without a robust firewall in place, your systems become vulnerable to attacks such as malware, ransomware, and data breaches that can significantly compromise sensitive information.
Moreover, the importance of firewalls extends beyond simple traffic control. They also provide vital security features that can include logging and reporting, intrusion detection, and prevention mechanisms. By regularly analyzing firewall logs, organizations can identify suspicious activities and act swiftly to mitigate potential threats. In an increasingly digital world, investing in a reliable firewall solution is not just a choice; it is a necessity for maintaining the integrity and security of your network.
How to Identify Phishing Scams: Tips for Safe Online Browsing
Phishing scams are becoming increasingly sophisticated, making it essential for users to learn how to identify them to ensure safe online browsing. One of the key indicators of a phishing attempt is the sender's email address. Always check the domain of the email address, as legitimate organizations use official domains. Additionally, pay attention to grammar and spelling errors in the email content; many phishing emails contain unusual phrases or typographical mistakes. Another red flag is an email that creates a sense of urgency, prompting you to take immediate action. Always take a moment to verify the legitimacy of such requests before clicking on any links.
Another effective method for identifying phishing scams is to hover your mouse over links without clicking them. This will reveal the true URL, allowing you to check if it matches the intended website. Additionally, be wary of unsolicited messages that ask for sensitive information, such as passwords or social security numbers. It’s best to directly visit the organization's website by typing the URL into your browser rather than clicking on links provided in emails. Lastly, consider using security software that offers phishing detection capabilities to further assist in recognizing potential threats while you browse online.